February 17, 2021 Threat Alert: TeamTNT Pwn Campaign Against Docker and K8s Environments 本文共有3782个字,关键词:Docker、K8s、security Last week, TeamTNT launched a new campaign against Docker and Kubernetes environments. Using a collection of container images that are hosted in Docker Hub, the attackers are targeting misconfigured docker daemons, Kubeflow dashboards, and Weave Scope, exploiting these environments in order to steal cloud credentials, open backdoors, mine cryptocurrency, and launch a worm that is looking for the next victim. In this blog, I will explore these container images and what they were designed to do. The Docker Hub account ‘heavy0x0james’ was created on June 3rd, 2019. In February 2021, the adversaries uploaded six malicious container images that have been observed to perform attacks in the wild. All six container images initially run a shell file named init.sh, but in each image it does something different. Then the attackers leverage a binary named zgrab (MD5= 7691c55732fded10fca0d6ccc64e41dc) in order to scan the internet for more victims. Below is the list of these malicious container images and their capabilities: 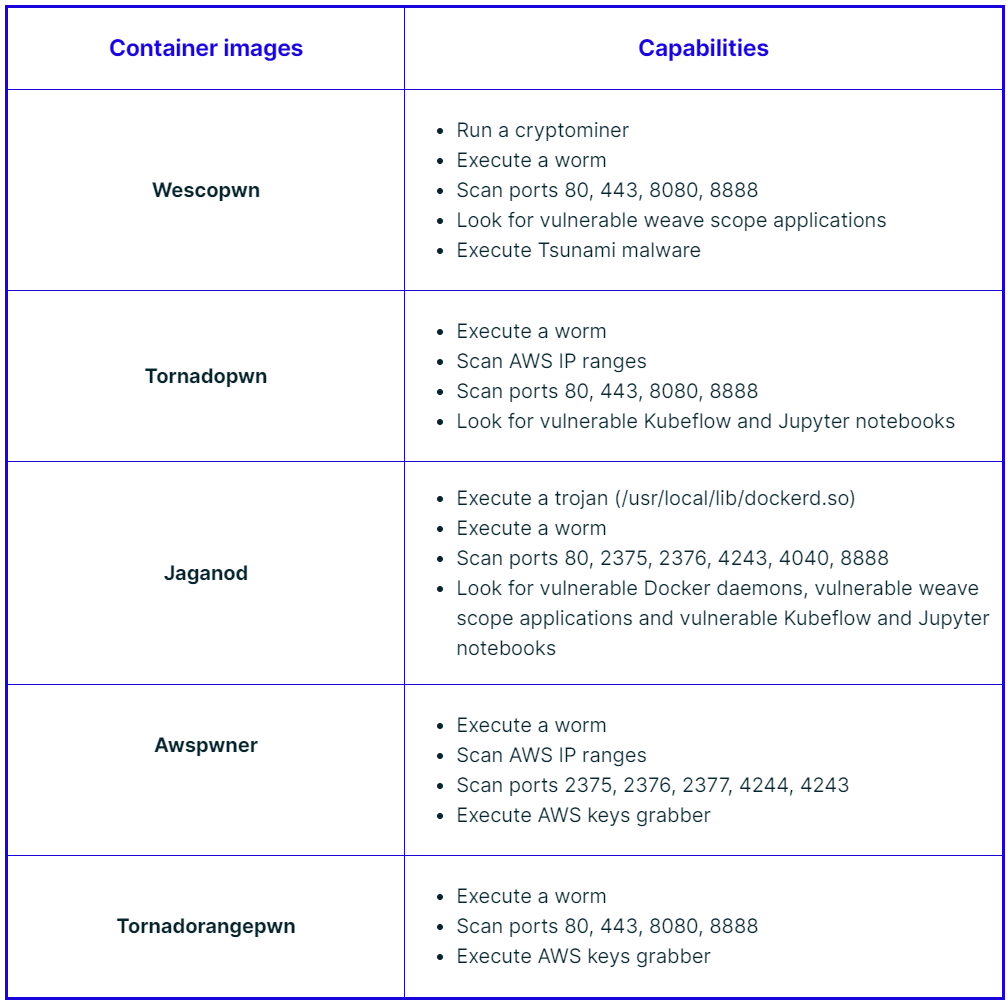 #### Conclusion Over the last few years, we at Team Nautilus have detected many kinds of attacks against Docker and Kubernetes environments, but this is the first time that we see a campaign designed to massively and systematically scan the internet, search for specific misconfigurations or outdated software, and attack the potential victims. Some of these images deploy a cryptominer, some open backdoors, and others are looking to steal AWS keys. These findings should alert security practitioners that even the smallest misconfiguration even for a fraction of time matters as it can result in a cyberattack. When working with Docker and Kubernetes environments, we recommend following these security best practices: 1. Regularly update your cloud software, specifically Docker and Kubernetes projects. Previous versions typically have more known vulnerabilities. 2. If possible, avoid exposing unnecessary APIs to the internet. Additionally, try limiting APIs inbound and outbound traffic to your organization’s network range. 3. Review authorization and authentication policies, basic security policies, and adjust them according to the principle of least privilege. 4. Regularly monitor the runtime environment. This includes [monitoring the running containers](https://www.aquasec.com/products/container-security/ "monitoring the running containers"), their images, and the processes that they run. Investigate logs, mostly around user actions, look for actions you can’t account for regular anomalies or outliers. 5. Implement a security strategy where you can easily [enforce your policies](https://blog.aquasec.com/cloud-native-security-drift-prevention "enforce your policies"), as well as consider using [cloud security tools](https://www.aquasec.com/products/aqua-cloud-native-security-platform/ "cloud security tools") that will widen your scope and reach within your cloud resources. ``` Indication of Compromise (IOCs) heavy0x0james/dockgeddon:latest root/dockerd (MD5= 091efbe14d22ecb8a39dd1da593f03f4) root/TNTfeatB0RG (MD5= 624e902dd14a9064d6126378f1e8fc73) C2= 45[.]9[.]148[.]85 heavy0x0james/wescopwn:latest root/dockerd (MD5= 091efbe14d22ecb8a39dd1da593f03f4) root/TNTfeatB0RG (MD5= 624e902dd14a9064d6126378f1e8fc73) C2= 45[.]9[.]148[.]85, borg[.]wtf heavy0x0james/tornadopwn:latest C2= 45[.]9[.]148[.]85 heavy0x0james/jaganod:latest usr/local/lib/dockerd.so (MD5= e8b1dc73a3299325f5c9a8aed41ba352) root/dockerd (MD5= 091efbe14d22ecb8a39dd1da593f03f4) C2= 45[.]9[.]148[.]85 heavy0x0james/awspwner:latest aws.sh C2= borg[.]wtf heavy0x0james/tornadorangepwn:latest aws.sh C2= borg[.]wtf ``` × yihong (๑>ڡ<)☆谢谢老板~ 2元 5元 10元 50元 100元 任意金额 2元 使用微信扫描二维码完成支付 版权声明:本文为作者原创,如需转载须联系作者本人同意,未经作者本人同意不得擅自转载。 码农心得,安全相关 2021-02-20 评论 3111 次浏览